Featured
ZK/SEC
June 28, 2025
1 min read
educative
TEE
security
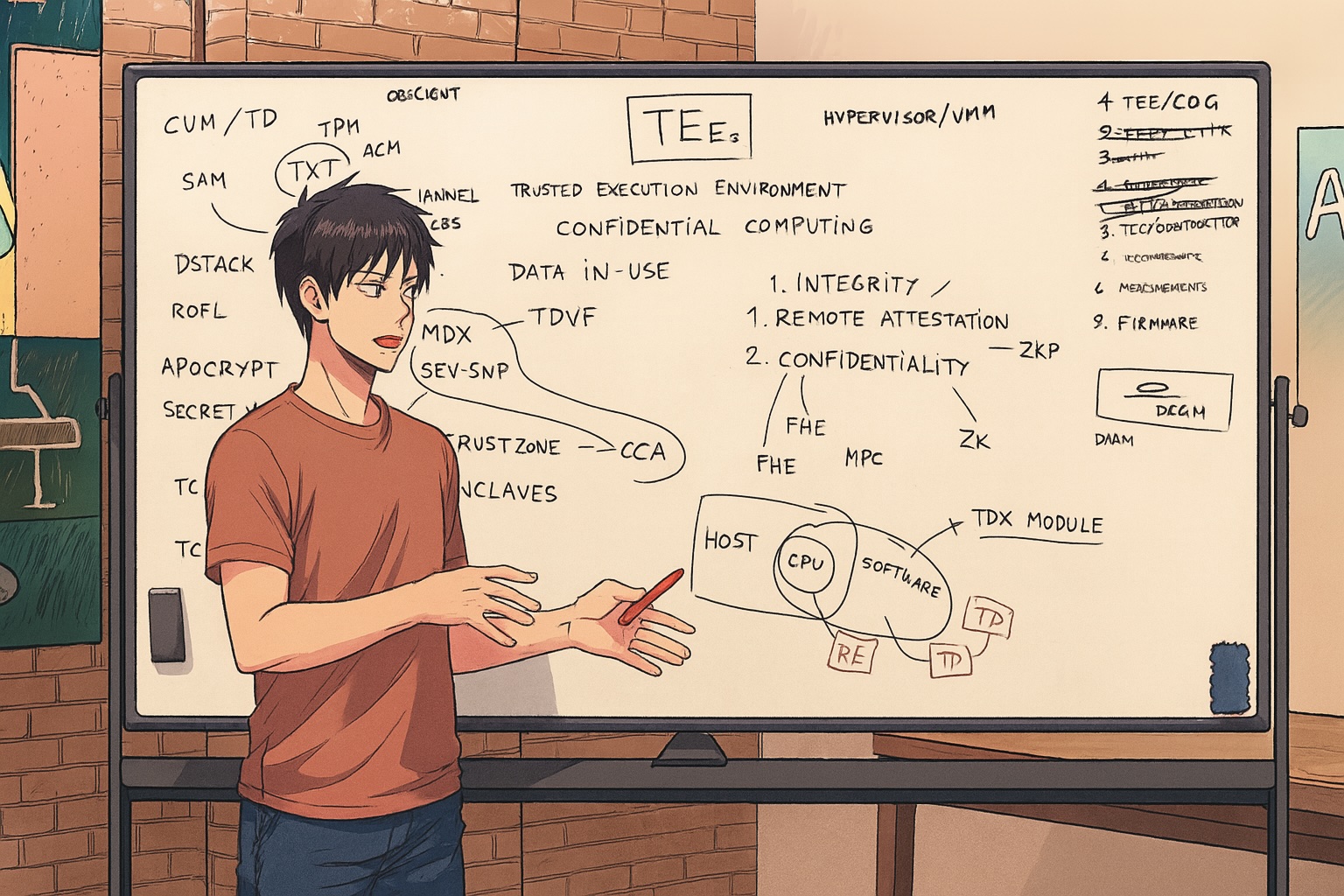
In the latest session of "Proof is in the Pudding," we teamed up with Archetype to explore the basics of Trusted Execution Environments. Through a collaborative whiteboarding session, we break down key concepts and practical applications, making this tech topic accessible and engaging. Dive in to discover how these environments can enhance digital security in a straightforward way.
Read →

Suneal Gong
June 26, 2025
9 min read
security
zk
solana
In June 2025, we uncovered a serious soundness issue in Solana's ZK ElGamal Proof Program that could let attackers manipulate confidential token transfers undetected. We worked with the Anza team to quickly address the flaw by pausing and disabling vulnerable components. This post dives into the root cause, which was a subtle mistake in handling prover-generated challenges within sigma OR proofs, revealing broader lessons in zero-knowledge protocol security. If you're interested in cryptographic protocol design, this could provide valuable insights.
Read →
Marco Besier
June 24, 2025
12 min read
educative
security
zk
tools
circom
Programming in Circom comes with its fair share of challenges. After reviewing numerous Circom codebases, we’ve identified certain anti-patterns that occur frequently. In this series, we’ll provide a comprehensive overview of these issues to help you avoid the most common pitfalls. Of course, this won’t be a complete list of every mistake possible (Circom has plenty of ways to trip you up). But the footguns we’ll cover are the ones that tend to catch developers off guard the most.
Read →

ZK/SEC
June 03, 2025
19 min read
educative
zk
pqc
lattice
In this engaging blog post, we dive into the future of cryptography by exploring how lattice-based proof systems could fend off the quantum threat. We break down Greyhound, a promising lattice-based solution, explaining its transparent nature, efficient construction, and adaptability with today's systems. Along the way, you'll get a glimpse of key concepts like lattices, Ajtai commitments, and how Greyhound cleverly ensures security and efficiency. Whether you’re curious about the cutting-edge of cryptographic research or just want to understand the basics of quantum-resistant solutions, this post offers both depth and clarity.
Read →
Suneal Gong
May 01, 2025
10 min read
educative
In this blog post, we explore an optimization for Barrett reduction, a popular method for modular arithmetic. We discovered that the error bound can be tighter than traditionally thought, meaning you often only need a single subtraction instead of two. This tweak can speed up cryptographic operations like those in the RustCrypto library by 14% when applied to NIST curves, which is a game changer for both encryption and performance. Dive into the details to see how this simple change can lead to significant improvements in real-world applications!
Read →
Varun Thakore
April 28, 2025
17 min read
educative
zk
In this blog post, we dive into the world of polynomial commitment schemes (PCS), which are crucial for constructing most practical SNARKs. We cover the basics of how PCS works, focusing on KZG10, known for its efficiency in proof size and verification time. You'll learn about the essential properties of binding and hiding and explore technical concepts like homomorphism, batching, and unconditionally hiding. We break down various methods to achieve these features, offering insight into how PCS maintains the security and privacy of polynomials in cryptographic systems. Get ready to understand these powerful concepts and their applications in modern cryptography!
Read →
Jaehun Kim, Jason Park
April 25, 2025
20 min read
educative
tools
zk
zkvm
Hey there! We're diving into how leveraging WebGPU can revolutionize client-side proving for privacy-preserving zero-knowledge apps. By tackling the usual time and memory bottlenecks with innovative techniques like using GPUs, we're achieving significant performance gains. We'll share our experiences using WebGPU with various frameworks, offering insights into optimizing operations and managing data transfer efficiently. Plus, learn about the challenges and exciting potential of integrating WebGPU into zero-knowledge frameworks. Join us to explore the future of privacy tech!
Read →



