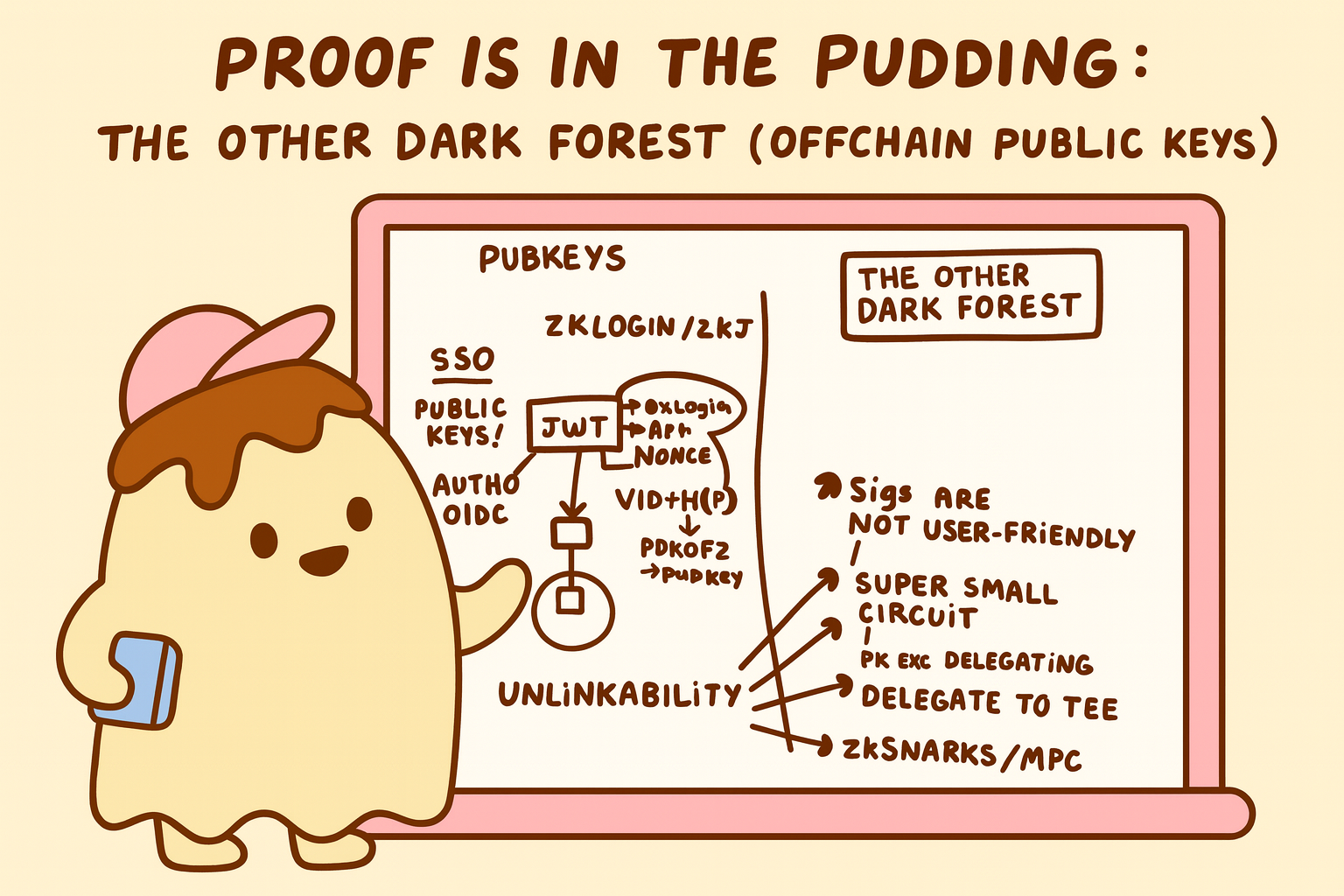
For the 7th session of Proof is in the Pudding, we teamed up with Archetype to explore the fascinating realm of offchain public keys—what we call "the other dark forest."
In this session, we examined how protocols like zkLogin, ZK Email, and ZKPassport handle authentication using offchain cryptographic keys. We explored the fundamental challenge of unlinkability in privacy-preserving protocols and discussed how replacing traditional signature verifications with zero-knowledge proofs can enable more powerful and interesting ZK applications.
We covered:
- zkLogin: How Sui's zkLogin enables wallet creation using familiar OAuth credentials like Google or Apple IDs, discussing the architecture and security model behind proving OAuth JWT signatures in zero knowledge
- Client-side proving: The practical considerations and trade-offs of generating proofs on user devices versus server-side proving
- Verifying signatures in ZK: The technical challenges and opportunities that arise when you verify cryptographic signatures inside zero-knowledge circuits
- ZK Email: How zero-knowledge proofs can be used to verify email authenticity while preserving privacy, enabling use cases like anonymous proof of email domain ownership
- ZKPassport: How biometric passports with digital signatures can be verified in zero knowledge, and the broader landscape of different authentication types and their ZK-friendly properties
- Selective disclosure: How ZK proofs enable users to prove specific claims about their credentials without revealing the underlying data
This session provides a comprehensive look at how zero-knowledge proofs are transforming authentication and identity systems by enabling privacy-preserving verification of offchain credentials.
If you enjoy this video, check out our previous episodes:
- Session 01: Arithmetization - Introduction to converting logical statements into arithmetic circuits
- Session 02: zkTLS - Exploring zero-knowledge TLS and secure oracles
- Session 03: How to Prove False Statements - Fiat-Shamir security and the GKR protocol
- Session 04: Proofs On A Leash - Introduction to post-quantum lattice-based SNARKs with Greyhound
- Session 05: Trust, But Measure - Introduction to Trusted Execution Environments with Intel TDX
- Session 06: Introduction to Data Availability Sampling - How rollups and Ethereum's DA system work